Information Gathering
here i use netdiscover to scan the network on interface vboxnet1
root@bt:~# netdiscover -i vboxnet1 -r 192.168.0.0/16
so we got two ip. 192.168.2.100 and 192.168.2.101
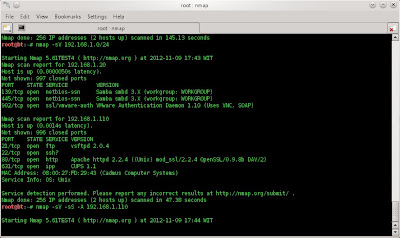
then scan the ip target using nmap
i also use scan using nikto
open the web page to see the content
Service Enumeration
based on the picture on nmap on ip 192.168.2.100, i found some port open, such as port 21 (ftp --> Anonymous ftp login allowed), 22 (ssh), 25 (smtp) 80 (http), 110 (pop3), and 143 (imap). and on ip 192.168.2.101, i found port 80 (http).
on nikto ip 192.168.2.100, i found directory icons and files index.php and info.php. but on ip 192.168.2.101 i found directory icons and /~root/ and it allowed to browse root's home directoy.
and on the web page (ip 192.168.2.100) i found some names.
and on ip 192.168.2.101 i just found some files.
Vulnerability Assement
i've tried to enter through ftp, but it not successfully access it.
based information on nikto i try to access on directory ~root. and i guess there are some directory users.
so i will make list of user based on iformation that i found on the web page and i save it with name user.
Exploit
here i use dirbuster to looking for directories and files and also will scann use my user list.
and i found some interest directory (~pirrip, ~magwitch, and ~havisham)
then i use nikto again to see any directories and files that exist in directori ~pirrip.
root@bt:/pentest/web/nikto# ./nikto.pl -host http://192.168.2.101/~pirrip/ -Display 1
i found a hidden folder .ssh/
so open it in browser.
i found the private and public ssh key for pirrip. so download it and save it to directory ./ssh (on my backtrack) and then change the permissions. then, enter into the system via ssh.
so i was in the system, so try to access the /etc/passwd and /etc/shadow/ to see the password root.
i have a problem, because permisson denied, and also i don't know the pirrp's password. so i will exploring some folders to search information. and found interestin file on /var/mail/. here i found pirrip's mail.
and at the end (message), i found pirrip's password.
so i try to gain root access using pirrip password, but it not works. so type sudo -l to see list of command that may run.
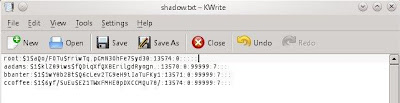
here vi is allowed i used it to see /etc/shadow. then i will use jtr to crack the password.
it is so long i waiting to crack the password using jtr, so i try to change the password root be pirrip's password.
then gain the access root.
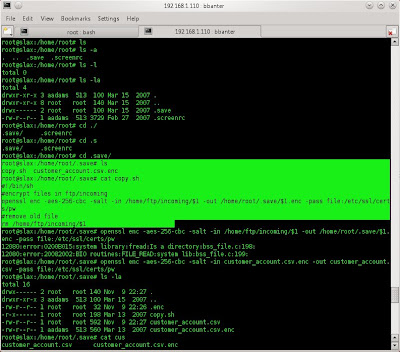
i was on root, based on previously challange, we have to get information about account bank or credit card. so try to do exploring in some folder again. and i found a file zip on /root/.save. so i unzip it but the file still compressed by tar. so uncompress it again. and found an interesting file, that is a mail text (Jan08).
here i use cat to see the content and i found data for raises for they tim.
Alhamdulillah ... :D