Service Enumeration
based on the picture, i found 2 host
192.168.1.20 that's my ip and 192.168.1.100 is ip target, and I also
found some port open, such as port ftp (but the ftp is broken), ssh, smtp, http, pop3, and
imap. And some vulner of PHP, etc.
-->
Vulnerability Assasement
So I try to use exploit db to search
exploit for the vulnerability and I found 1 exploit for ssh 4.3 but
it not works to enter into the system.
-->
Exploit
In the web page, I found some names, so
I will try to make a list of users and I will use it to brute force
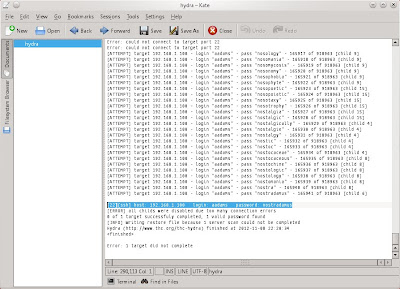
the ssh. Here I use hydra to brute force the ssh service.
I found username and password for ssh.
then enter into the system use user
bbanter and password bbanter via ssh.
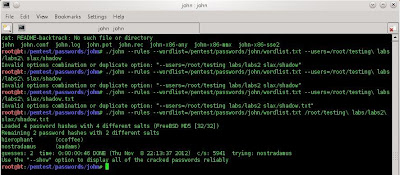
I try to see the /etc/shadow because
I'm not on the root but I have a problem with the permission so I try
to see the /etc/passwd to see the users.
I founds some user and save it. Then I
will brute force the ssh using hydra again to gain high permissoin
because on user bbanter I can't do many thing.
then save the output. Here I found
password nostradamus for user aadams.
Try to connect via ssh again using
aadams and password nostradamus.
Then I try to see the /etc/shadow/
until here I successfully gain high
access (on root). But the hint on the web page, we have to get the
CEO's bank account information.















No comments:
Post a Comment