here i will use nmap for scanning the network.
Service Enumeration
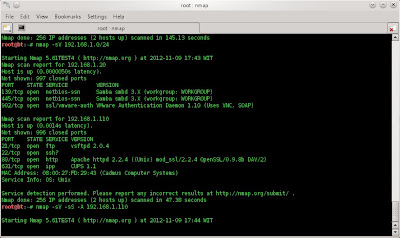
based on the picture, i found 2 host 192.168.1.20 that's my ip and 192.168.1.110 is ip target, and I also found some port open, such as port 21 (ftp), 22 (ssh), 80 (http), and, 631 (ipp).
Vulnerability Assasement
based of the Information Gathering, we can see that on port 21 (ftp), we can login using anonymous and there are two folder (downloads and incoming).
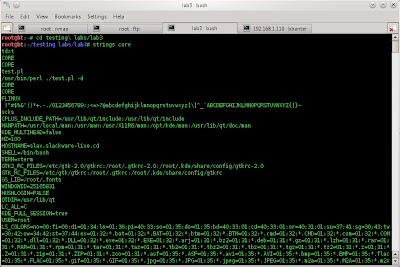
then, download the file core, and use string to see the content.
i found like /etc/shadow at the end of file core. so crack it using john the ripper for login via ssh.
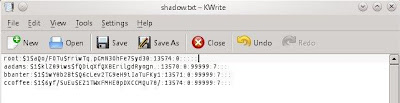
here i will cutting the file core that i will crack like shadow. and then crack it.
i successfully crack it, i found the password for root and password for the other user.
so, try to log in through ssh using other user but not using root, because in this lab, we can't enter using root. but don't worry, we can gain the root using other user because we have password root. :D
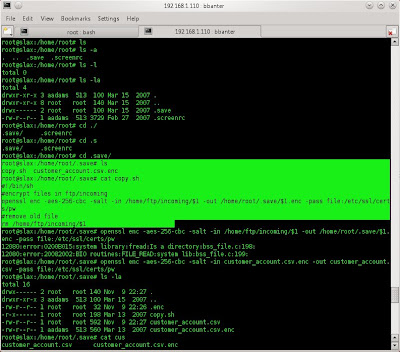
i successfully gain the root, but the hint on the web page, we have to get the customer credit card. so search it on every folder. after i seach on every folder, i found it on folder home/root/.save/ . and use command ls -a to show all folder, because folder .save is a hidden folder.
and i also found the key for open the file customer_account.csv.enc because the file is encrypted using openssl. so execute it and don't forget to set -d option for decrypt it.
it works and i successfully decrypt the file. now we can see the customers credit card.
Alhamdulillanh ... :D








No comments:
Post a Comment